A Tale of Social Media Recovery Scams
A chat with a threat actor who scams victims of social media account takeovers
Once upon a time, there was a rising trend of social media recovery scams…
These scams target people who have lost access to their social media accounts, through lack of access to email accounts or they were hacked/taken over, and are desperately seeking help to regain control. Scammers then take advantage of their vulnerability and promise swift and guaranteed account recovery in exchange for payment. These payments ranged anywhere from $20-$100 depending on what the account is and how desperate the person appears to be.
In 2022, the Identify Theft Resource Center (ITRC) received four times the number of inquiries compared to 2021 and 40 times more inquiries than in 2020. While many social media account takeovers are on Instagram, plenty of attacks occur on other platforms, such as Facebook and LinkedIn.
Unlike your traditional hackers, these threat actors are fully focused on social engineering concepts and may not even have technical skills beyond their con. The process is simple and is triggered by the person’s own urgent request for help. They post on forums or other social media sites, and in comes your friendly, totally legitimate white hat hacker who can help recover your account. But of course, they can’t do anything, and will take your money and run.
Typically the threat actor will exchange some basic information, occasionally create a fake process that makes it look like they are checking into your account, and then will request funds before recovering the account. During this process, would be victims can be hit for more than just money, too. They may be asked for additional usernames, passwords, or direct information to access your financial accounts.
With this all in mind, let’s meet one of these threat actors.
Meet ‘Frank’, the LinkedIn Account Recovery Scammer
**Please note that you should not interact with threat actors and scammers. It increases the likelihood of retaliation and other unnecessary outcomes. Further, it is against the Computer Fraud and Abuse Act to counter-attack threat actors.
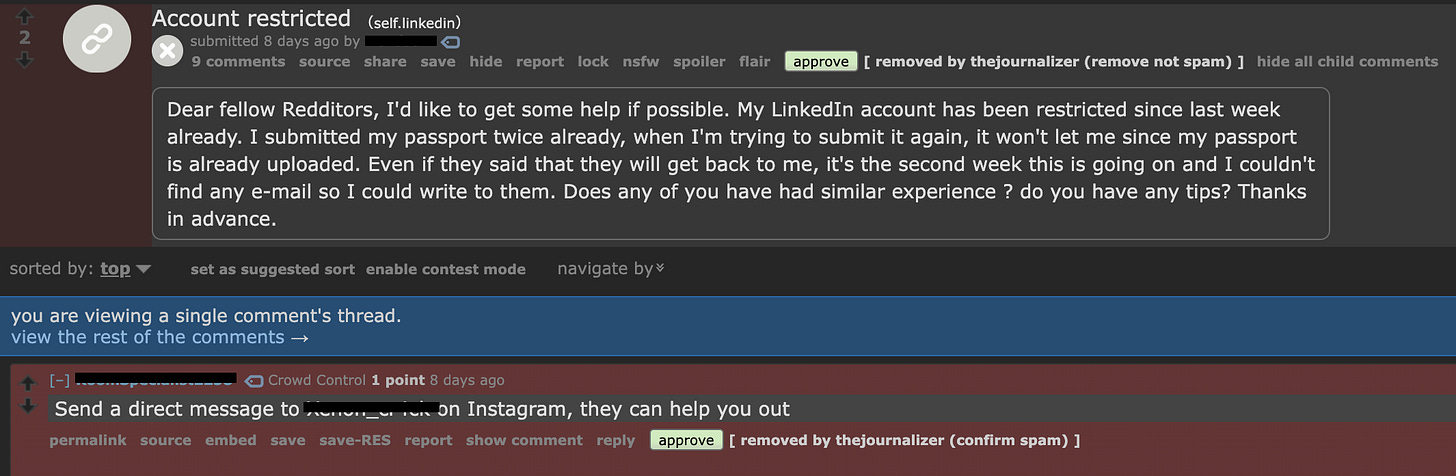
In the past three months there has been a dramatic increase in support requests on the LinkedIn subreddit to help recover accounts. User accounts are being frozen, taken over, or banned. With social customer support systems often more than stretched thin and taking a significant amount of time, these users will seek out forums and other guidance to expedite the process. With each post on the LinkedIn subreddit, anywhere from 2-5 recovery scammers will attempt to offer their services.
A majority of what you see here is a number of accounts dedicated to offering account recovery services. Here is a specific example of what this looks like:
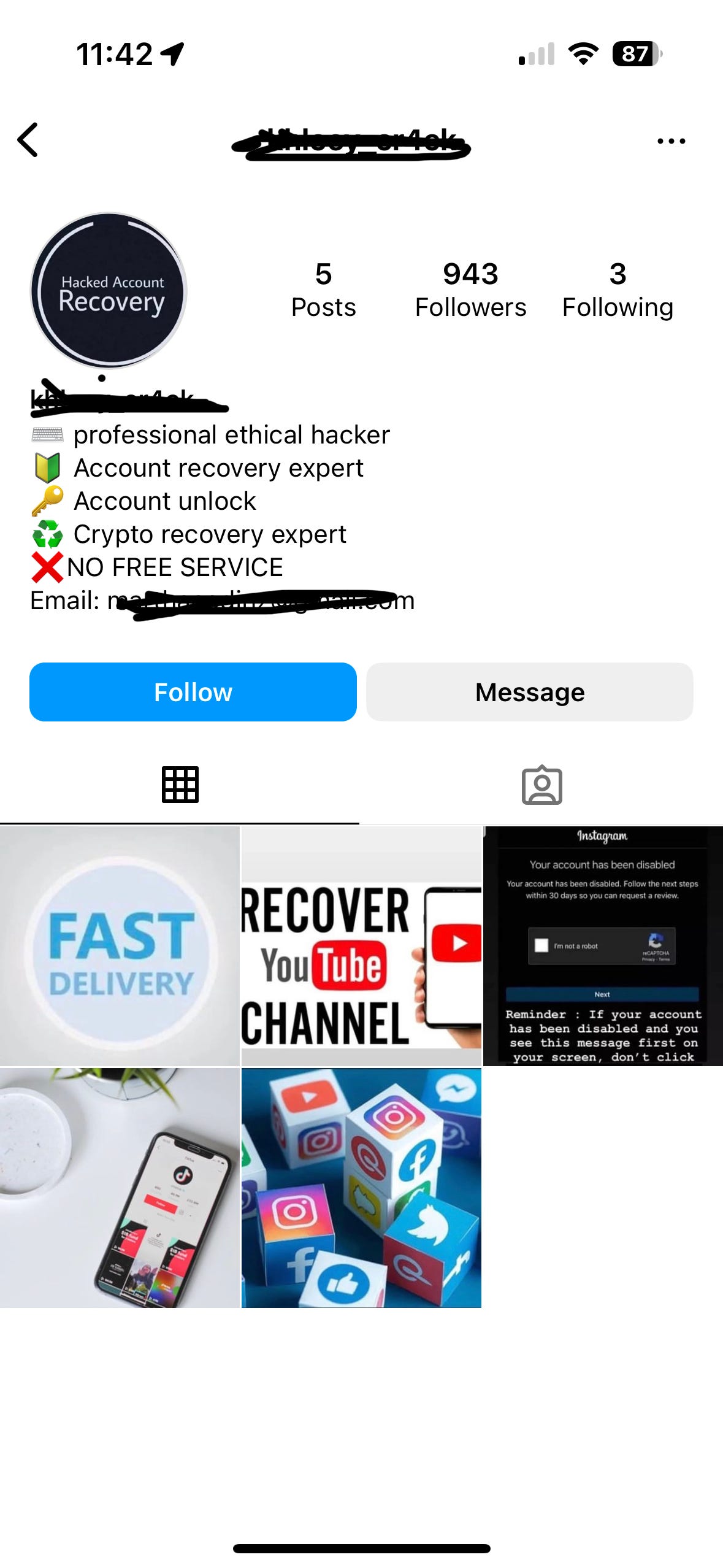
You can see the removed spam comment pointing the victim towards a particular Instagram account. I’m not sure why Instagram is their platform of choice, but in the past 3 months, it’s always there. When you go to the account in question, the person poses as a white hat hacker who can recover your account.
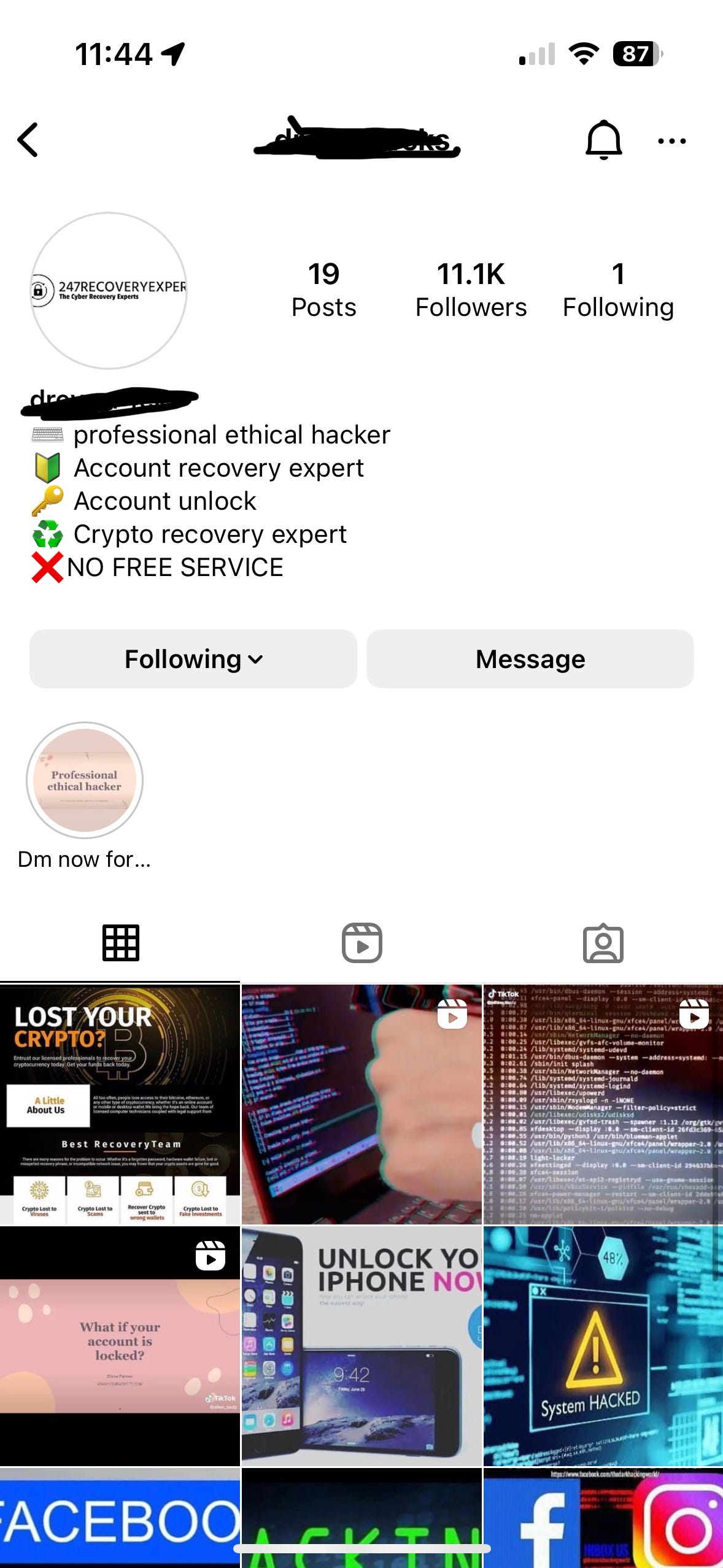
I reached out to two, both that used similar message prompts and had similar naming conventions for their Instagram name. Again, please don’t do this yourself.
The first account belongs to ‘Frank’ the second one is ‘Drey’ and both offer account recovery services for social media or crypto accounts. For now, we’ll focus on Frank.
We start the chat by telling Frank that my LinkedIn account had been taken over, and I needed support.
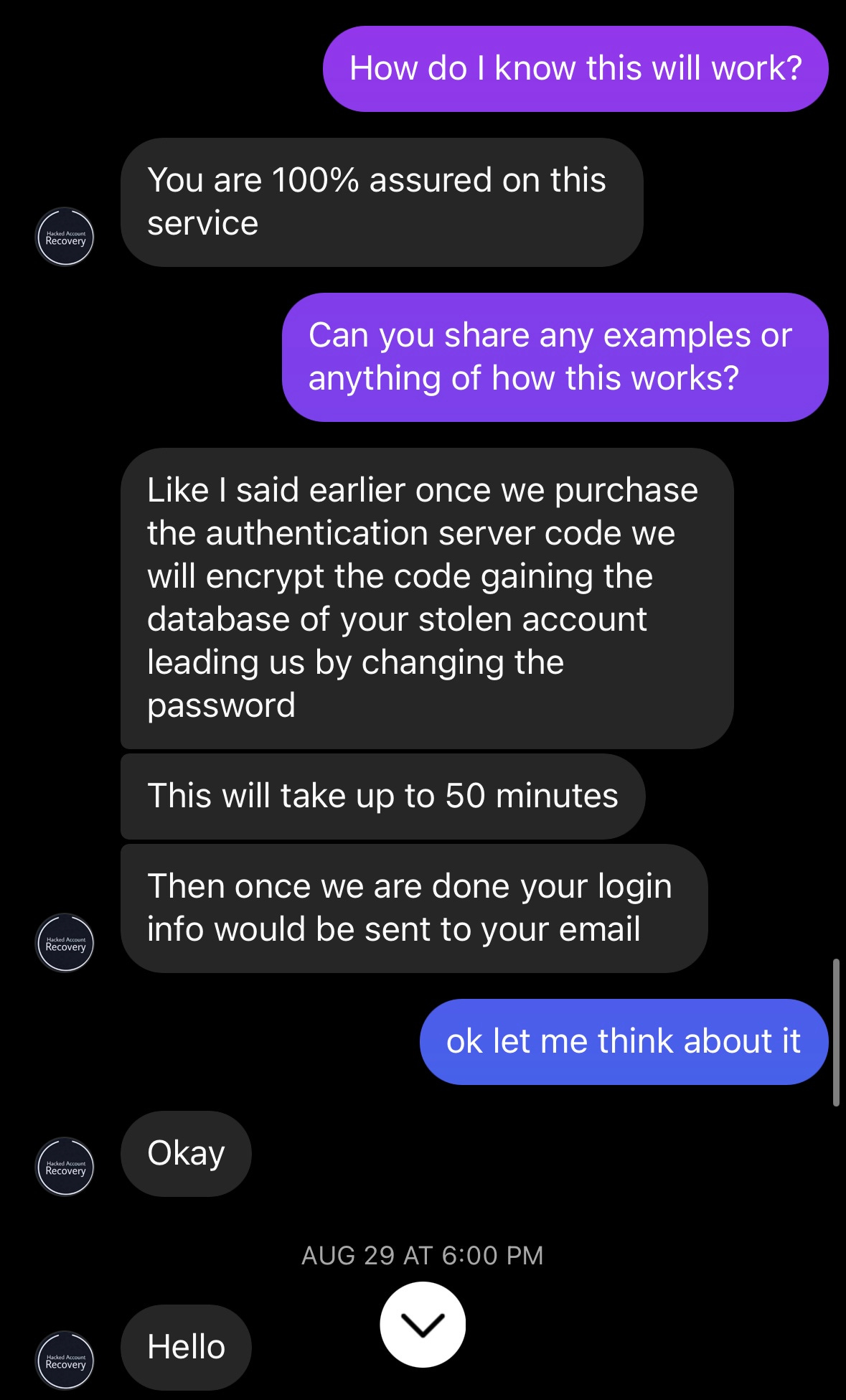
Almost immediately, Frank makes it clear that his services are not free. That he would have to get an authentication server code. That’s not really a thing, but it sounds like he’s trying to say he can send an OTP or one-time password to your device to verify that it’s your account and get you access. This is essentially what the platform would do if you had 2FA on, but some external party can’t trigger that, especially if you don’t have it on already.
So I ask how I know this process will work, Frank says he will guide me through the process, and it’s time to fork over the cash. Not exactly exuding confidence. Time to double down.
Frank, this script is worse than most hacker movies. Come on bud. Anyway, it was time to ghost Frank and string this along. Every day, several times a day, Frank would message me asking if I would like to proceed. About a week later, it was time to unmask our friend. Instagram makes it difficult to send links of a certain nature, so I moved Frank over to WhatsApp where I was able to hit the uno reverse card. I used social engineering to get him to click a link, and in doing so, was able to capture some information about him. We’ll get to that in a moment.
From here, I told Frank the scoop, and he took it exceedingly well…
Frank’s bad hacker script-writing skills can’t even come close to his graphic design skills. To his credit, at least he didn’t add an extra T to my name. It was at this point I told him that he was in Nigeria, using a Samsung Galaxy A50, and generally knew his whereabouts. Oops.
Anyways, I made it clear to Frank that I was just trying to have a chat with him, to understand why he was going after victims. From here, we can take most of this with a huge grain of salt, because it was clear he wasn’t being all that truthful. So who is our friend?
Young, most likely under 25 based on some comments made. He supposedly lives on the streets and is attempting to do this to survive as he has no parents. His passion is becoming a footballer. He was apparently doing this completely on his own and not part of any group.
With some clarifying questions, it was abundantly clear that most of this was fictitious, except maybe the football part. This brings us back to Drey, the other Instagram white hat hacker. Now that the cat was out of the bag, I was attempting to get them to move over to WhatsApp to pull the same card, and they of course, just happened to no longer have an account there anymore. My spidey sense tells me they are working together, if not the same person, but their choice of words and language were significantly different after the initial prompts.
At this point, Frank said his days of scamming people were over.
Frank’s primary Instagram account hasn’t been updated since, but it only took a day or two before a new account was listed as an account recovery expert back on reddit. Oh, Frank. Meanwhile, he did ask if I knew of any remote jobs that he could do, so there was that.
Social Media Account Takeovers Always on the Rise
Since the early days of LiveJournal (DeadJournal for me), Myspace, and Friendster, social sites have always been ripe for social engineering. Less tech-savvy users are quick to trust people they elected to connect with, including family, and will click on malicious links sent to them. From there, the cycle goes on and on.
The above provides a 12-month look at search results for top social platforms and user accounts being taken over. That spike for Snapchat around August 17 is a good example of impact as its users thought the new AI bot was compromised due to it posting a Snapchat Story. They denied the account/platform was compromised. Facebook and Instagram take the largest piece of the pie.
What Causes the Increase in Social Media Recovery Scams?
For starters, the social media account takeover market is significant and has been since the early days of social media. Threat actors are keen to takeover social accounts because they have a history of appearing as a real person, and you can then use social engineering to send malicious links/lures to propagate the attack further or ask for financial support by posing as a friend or loved one. Combine this with constant password re-use and a lack of user adoption on 2FA/MFA, and you have a lovely scenario where every breach the masses get hit by, their now compromised email and re-used password is just sitting there ripe for the taking.
According to ITRC:
Between April 2021 and March 2022, 85 percent of reported victims had their Instagram accounts compromised. Seventy (70) percent of victims had been permanently locked out of their social media accounts, and 71 percent of victims reported the criminals had contacted additional friends listed in the ‘friends’ list of their social media accounts. Sixty-seven (67) percent reported that the criminals continued to post as the account owner after they were locked out.
That is a lot of people trying to regain access to their accounts, many of whom may not be adept at spotting scams and social engineering.
This is where the recovery scammer steps in. They know these platforms typically take days, if not weeks, to respond. From there, it takes even longer because these social giants have various ID verification systems, which pose a privacy issue in and of itself. Then you may be able to regain control of your account. However, by this time, most of your data, information, and connections may be dumped, so you will be starting from scratch.
Further, some platforms, LinkedIn in particular, is very particular about you not creating duplicate or alt accounts, and will ban it. This could impact your original account too, so you can’t just skip the process and start from scratch; you still need to wait the process out.
Because there is not much of a direct financial burden to these platforms, there is no urgency to increase support to recover accounts. Of course, this is where reputation damage comes into play, but since that is more challenging to track with metrics, they can turn a blind eye toward the situation.
Avoiding Social Media Social Engineering and Account Takeovers
This part is easy, especially since most of the AZT audience works in cybersecurity, so this is more for you to encourage others.
Stop reusing passwords. Use something like 1Password or Bitwarden.
Use complex passwords, even better if randomly generated.
Use 2FA/MFA if available, and don’t use the SMS option.
How to Recover your Hacked Facebook, Hacked Instagram, or Hacked LinkedIn Account
The only way to recover your hacked social media account is through the official channels. Anyone outside of these platforms will just take your money and run. Simple as that.